During Thursday's Aspen Security Forum, Tom Burt, Microsoft's VP of Customer Security & Trust, warned the crowd that hacks, like those during the 2016 elections by Russian government operatives, continue to happen. Three midterm candidates already suffered cyber attacks from Russian hackers.
In 2016, Burt said his team discovered fake Microsoft domain names used by the Russian hacking groups —given code names like Scrontium, APT28, Fancy Bear and Pawn Storm— used to "phish" information from unsuspecting campaign staffers.
Phishing is defined as the fraudulent practice of sending emails or websites appearing to be from reputable sources in order to obtain personal information, such as passwords and credit card numbers, to gain access to a person's online data or accounts.
The Russian hackers in 2016 used their phished information to gain access to the Democratic National Committee (DNC) servers. They then stole emails and records from the DNC which led to further hacking.
The Russian intelligence operatives then leaked emails and private messages from the DNC as well as longtime Clinton aide Robert Russo and campaign chairman John Podesta. Russian operatives also famously contacted the Trump campaign with offers of damaging information about Hillary Clinton.
Through Wikileaks, the Russians released months of damaging disclosures about the Democratic Party’s nominee intended to influence the United States presidential election. The administration of President Barack Obama began looking into the Russian hackers in 2016 and the Trump administration continued the investigation through Department of Justice appointed and directed Special Counsel, Robert Mueller.
Now, in 2018, Burt stated during the cyber security conference, his team recorded the same phishing approach again.
Earlier this year, we did discover that a fake Microsoft domain had been established as the landing page for phishing attacks and we saw metadata that suggested those phishing attacks were being directed at three candidates who are standing for election in the midterm elections."
"We can’t disclose [their identities] because we maintain our customer privacy," Burt continued, "but I can tell you that they were all people who, because of their positions, might have been interesting targets from an espionage standpoint as well as an election disruption standpoint."
"We took down that domain, and working with the government we were able to avoid anybody being infected by that particular attack."
Burt's claims back up the announcement by President Donald Trump's handpicked National Intelligence Director, Dan Coats, who on Monday stated the Russians remained a viable threat to United States cyber security. Coats statement came after the President cast aspersions on U.S. intelligence agencies' clear evidence of Russian hacking by Tweet and during a joint news conference with Russian President Vladimir Putin in Helsinki, Finland.
Trump took considerable criticism for his remarks and issued a statement Tuesday saying he misspoke.
During the press conference in Helsinki, after the closed door private meeting with Putin, Trump said he didn’t "see any reason why it would be" Russia hacking the United States to influence the 2016 election. Due to severe criticism, Trump later claimed that he meant to say he didn't see any reason it "wouldn't" be Russia.
But on Wednesday the President again denied Russia was definitely involved in the known hacks and said Russia was no longer a threat because Putin knows he is very tough.
The engineers at Microsoft call the Russian directed hacking group Strontium, but intelligence agencies and cyber security experts also refer to them as APT28, Fancy Bear and Pawn Storm. Experts claim their activities intertwine with Russia’s military intelligence unit known as GRU.
While the hacking continues, as with many voters who skip midterm elections, Russian hacking remains at a lower intensity than during the lead up to the 2016 presidential election.
Burt also attributes the lower Russian hacking activity to seemingly lower stakes in the midterm elections where a presidency is not on the line. Burt stated,
"I would say that the consensus of the threat intelligence community right now is that we are not seeing the same level of activity by the Russian activity groups leading in to the midyear elections that we could see when we look back at the 2016 election."
"We don’t see the activity of them trying to infiltrate think tanks, academia and social networks to do the research they do to build the phishing attacks that they then launch," Burt explained. "We are not seeing ongoing activity like the one we were able to disrupt earlier this year."
But he also cautioned vigilance is still needed.
That doesn’t mean we are not going to see it, there’s a lot of time left before the election."
The United States intelligence community characterized the 2016 Russian cyber attacks as two pronged. The first employed bots to create social media misinformation campaigns against Hillary Clinton and in favor of Donald Trump. Social media outlets continue to work against this ongoing method of attack.
The second was the phishing to gain access to DNC records and internal correspondence, also designed to hurt the candidacy of Clinton and bolster Trump. Russian intelligence used supposed whistleblowing website WikiLeaks, contacting them via Twitter front account "Guccifer 2.0" in the second phase of their interference in the 2016 presidential election.
Since the 2016 elections, Special Counsel Robert Mueller's investigation resulted in over 100 criminal counts, 35 indictments, 5 guilty pleas and 4 convictions as of July 13.
The midterm elections are November 6, 2018. United States voters can mitigate the influence of foreign governments by performing due diligence on information online and casting their vote. In the 2014 midterms, only 38% of eligible voters bothered to cast a ballot.






 The Benny Show
The Benny Show





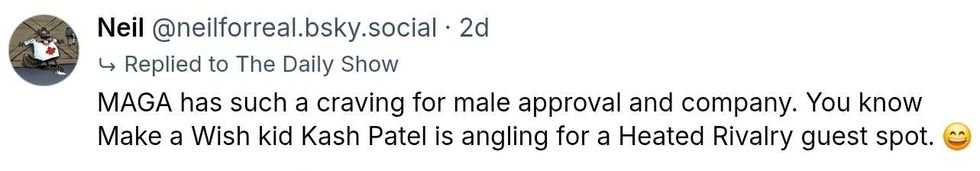 @neilforreal/Bluesky
@neilforreal/Bluesky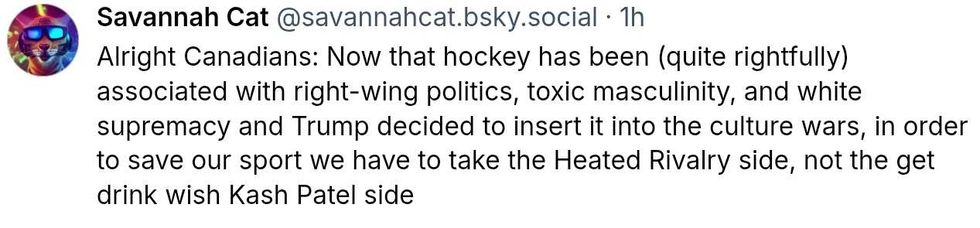 @savannahcat/Bluesky
@savannahcat/Bluesky @qadishtujessica.inanna.app
@qadishtujessica.inanna.app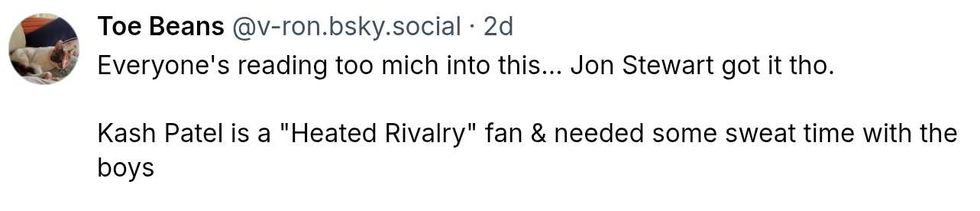 @v-ron/Bluesky
@v-ron/Bluesky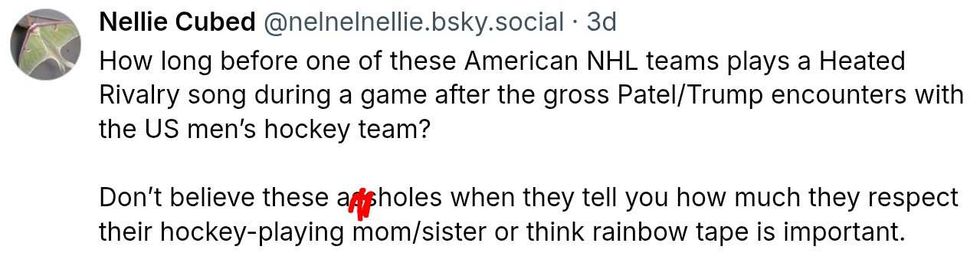 @nelnelnellie/Bluesky
@nelnelnellie/Bluesky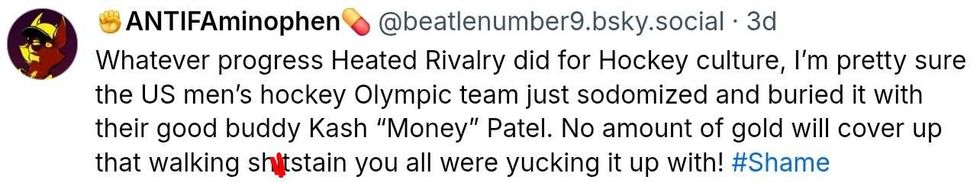 @beatlenumber9/Bluesky
@beatlenumber9/Bluesky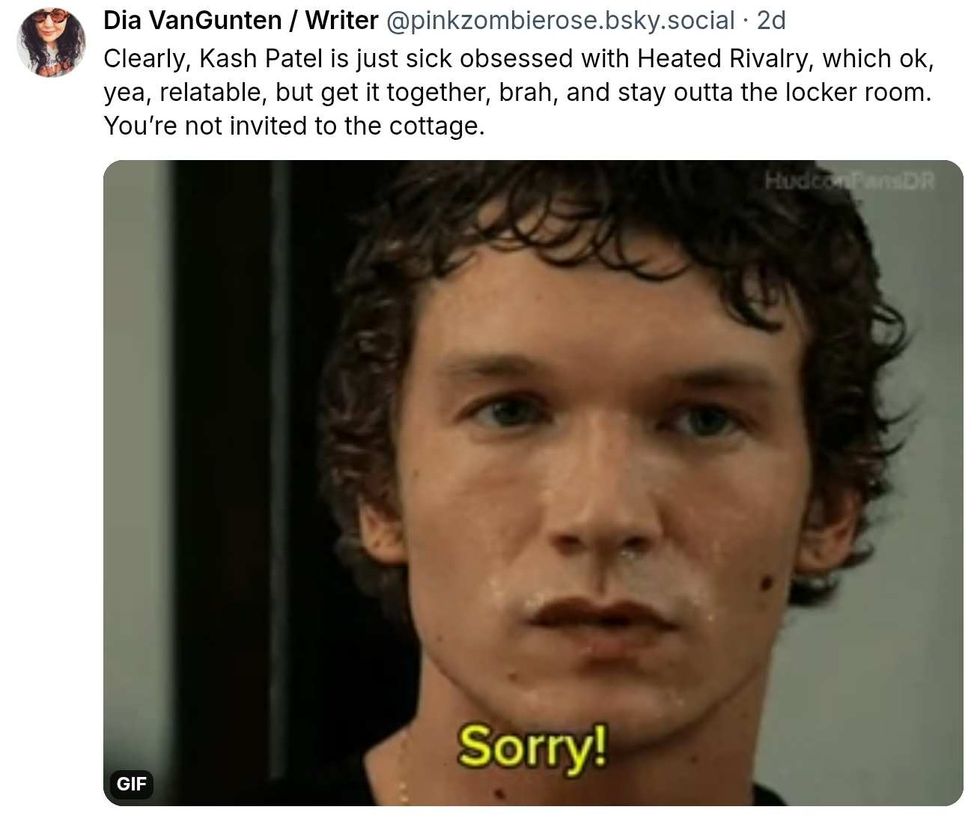 @pinkzombierose/Bluesky
@pinkzombierose/Bluesky
 @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok @theunobsolete/TikTok
@theunobsolete/TikTok
 @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok @laysuperstar/TikTok
@laysuperstar/TikTok